Encoding Vs Encryption Vs Hashing
In the digital field, most people usually finding it difficult to understand these THREE terminology. Encoding, Encryption and Hashing. It is common to hear some people using these terms in the wrong sense.
In this article, I will be dissecting the differences between Encoding, Encryption and Hashing.
Encoding
Encoding is to convert information from one format into another format
Example:
- UTF-8 encoding scheme is used to represent a character using 8 bits, 1 byte
- HTML Encoding: Html encoding is mainly used to represent various characters so that they can be safely used within an HTML document (as the name might suggest).
- URL Encoding: When dealing with URLs, they can only contain printable ASCII characters (these are characters with ASCII codes between decimal 32 and 126, i.e. hex 0x20 – 0x7E). However, some characters within this range may have special meanings within the URL or within the HTTP protocol. URL encoding comes into play when we have either some characters with special meaning in the URL or want to have characters outside the printable range
Reason for encoding
- Consumer system requires information in a particular format e.g .png instead of .jpg
- We may want to send a file over the network as a string of character. We may Base64 Encode this file content as a string data format and then send the data as string and on the receiving end we Base64 Decode data back into a file.
- I may want to reduce the size of the data before sending over the network or storing on my file system. Encoding scheme like Huffman encoding is a simple compression algorithm to represent information in smaller size
It is important to understand that every encoded data can be decoded by anyone. There is not special security on the data when we encode it.
If you want your data to be secured and prevent access to a specific group of people or just you. Then you will need to Encrypt your data.
Encryption
Encryption is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot.
If you noticed, the word/term encoding is used in the definition of encryption. This is because encryption represents the data in another format but this time in a secure way. A way that prevent access to just anyone to decode the data to it original format.
In every encryption scheme/algorithm, there is a key, that is passed to the algorithm to encrypt the data and another key that is used to decrypt the data back to it original form.
The different forms of encryptions is all about what/ how the key is been generated and shared.
There are generally two category of encryption algorithm. Symmetric and Asymmetric Encryption.
Symmetric Encryption
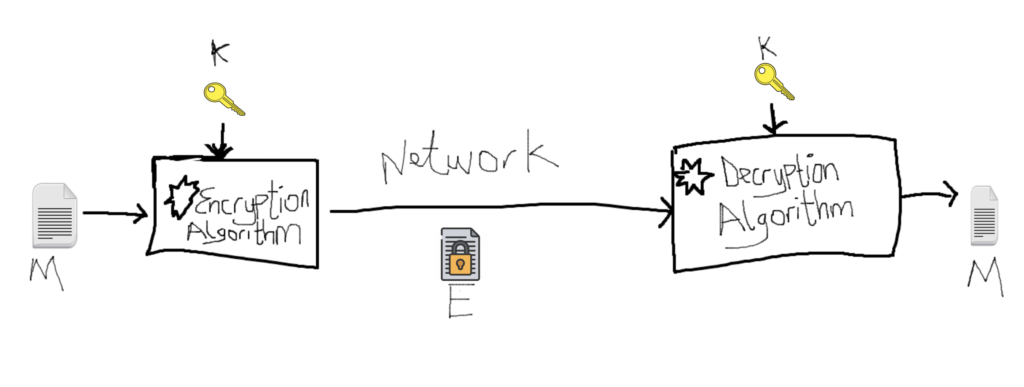
For symmetric Encryption, the information is encrypted with a particular key say KeyA and only KeyA can be used to decrypt the information to it original format.
Let say I have and message (M) and I need to send this message securely to another person over a network such that even if someone or some hacker over the network get this message, this person will not be able to get the original form of the message.
The original Message (M) is called Plaintext while the encrypted message is called Cyphertext (E).
If i am using a Symmetric algorithm, i will have to generate an encryption secrete key (K) and share this key with the recipient over another channel. Maybe email or a different network.
Before my messages are send to the recipient, i will encrypt it using this shared secret key (K) and send. When the recipient receive the messages it will decrypt it with the same shared secret key (K) to get the original Message (M).
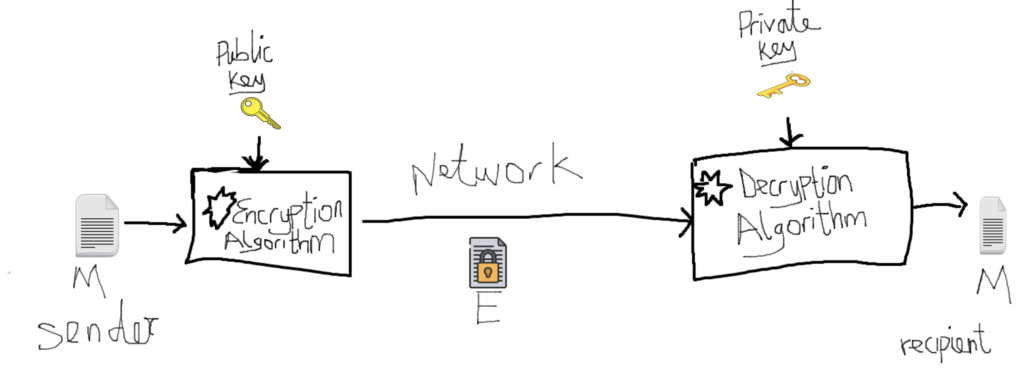
Asymmetric Encryption
Asymmetric encryption uses two keys, The private key and a public key. The key used for encryption is call the public key while the key use for decryption is call the private key.
In this method, the recipient has two keys, the private and public key. This recipient shares it public key to who ever wants to communicate. The sender will have to encrypt this message using the recipient’s public key and only the recipient with it secret private key can decrypt this information.
With this form of encryption, the recipient don’t bother about sending it secret key to anyone. But instead shared it public key to who ever need to communicate with it and only it private key can decrypt information encrypted by it public key.
Hashing
Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string. Hashing is a one-way processes meaning you can not get the original text from the hashed text.
Hashing is usually used for data integrity and validation. That is if you want to know if a particular data is different from the last time it was accessed. You can keep a hash value of the data from the time it was generated. if over time this data changed you will know by comparing the stored hashed value with the current hashed value.
You can also used Hashing to securely store user password in the database. Take for example you want to keep user’s password in the database but you don’t want your database admin to be about to know user’s password to your system. When user register on your system, you can store the hashed value of their password instead of the original one. In this way the DB admin will not be about to know the original password. When user logs in, with the username and password, you can hash this logged-in password and compare with the one stored in the database to grant access.
I hope this message was helpful to answer all your questions. Stay blessed and happy reading.
Thanks dear readers, I hope you like this topic. If you are a teacher or a student and you want me to do a write-up on something just like this one, send me an email to me@eddytnk.com with the topic.



Pretty! This has been an extremely wonderful article. Thanks for providing this information.
cols=Encryption : Encryption in encoding technique in which message is encoded by using encryption algorithm in such a way that only authorized personnel can access the message or information.